What is end-to-end encryption? End-to-end encryption (E2EE) is a security method where messages are encrypted on your device and can only be decrypted on the recipient’s device. No one in between, not the app company, not your internet provider, not hackers who intercept the data, can read the content. The encryption keys exist only on the devices at each “end” of the conversation, hence the name.
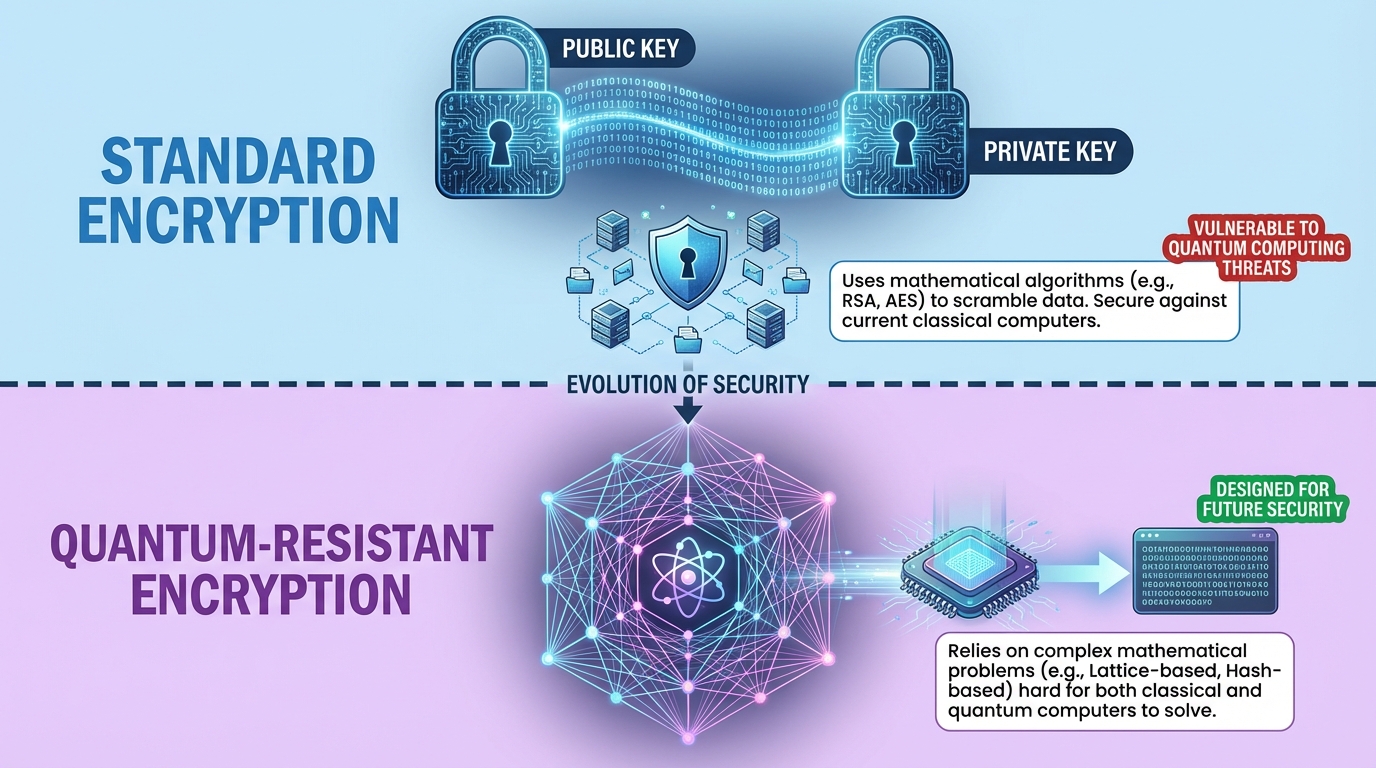
This differs significantly from standard encryption. When you use HTTPS to browse the web, your data is encrypted to the website’s server, but the server can read it. With end-to-end encryption, even the service facilitating the communication cannot access your messages. Apps like Signal, WhatsApp, and iMessage use end-to-end encryption for private conversations.
How End-to-End Encryption Works
To understand E2EE, imagine you want to send a secret message through the mail. With regular encryption, you’d lock the message in a box and send the key to the post office, trusting them to keep it safe and unlock the box only for the recipient. The post office can read your message if they choose.
With end-to-end encryption, you and your recipient each have two keys: a public key you share openly and a private key you never share. You encrypt your message using the recipient’s public key. Only their private key can decrypt it. Since they never share their private key with anyone, including the messaging service, only they can read the message.
The actual cryptography is complex, involving ephemeral keys and perfect forward secrecy, but the principle is simple: the keys to decrypt messages exist only on the sender’s and recipient’s devices. The messaging service acts as a courier carrying locked boxes it cannot open.
What End-to-End Encryption Protects
E2EE protects against several types of threats that standard encryption doesn’t address.
Company access: Without E2EE, the company running the messaging service can read your messages if they choose, whether for advertising, compliance with requests, or abuse by employees. E2EE eliminates this possibility entirely. Even if a company wanted to read your messages, they couldn’t.
Data breaches: If hackers breach the messaging company’s servers, they get only encrypted data they cannot read. Without E2EE, breaches expose actual message content. With E2EE, the stolen data is useless without the private keys stored only on users’ devices.
Legal compulsion: Governments can compel companies to hand over data. With E2EE, companies can only provide encrypted content they cannot decrypt. They literally cannot comply with demands to read specific messages because they lack the capability.
Man-in-the-middle attacks: Sophisticated attackers who intercept data in transit get only encrypted content. Without the private keys, interception is futile.
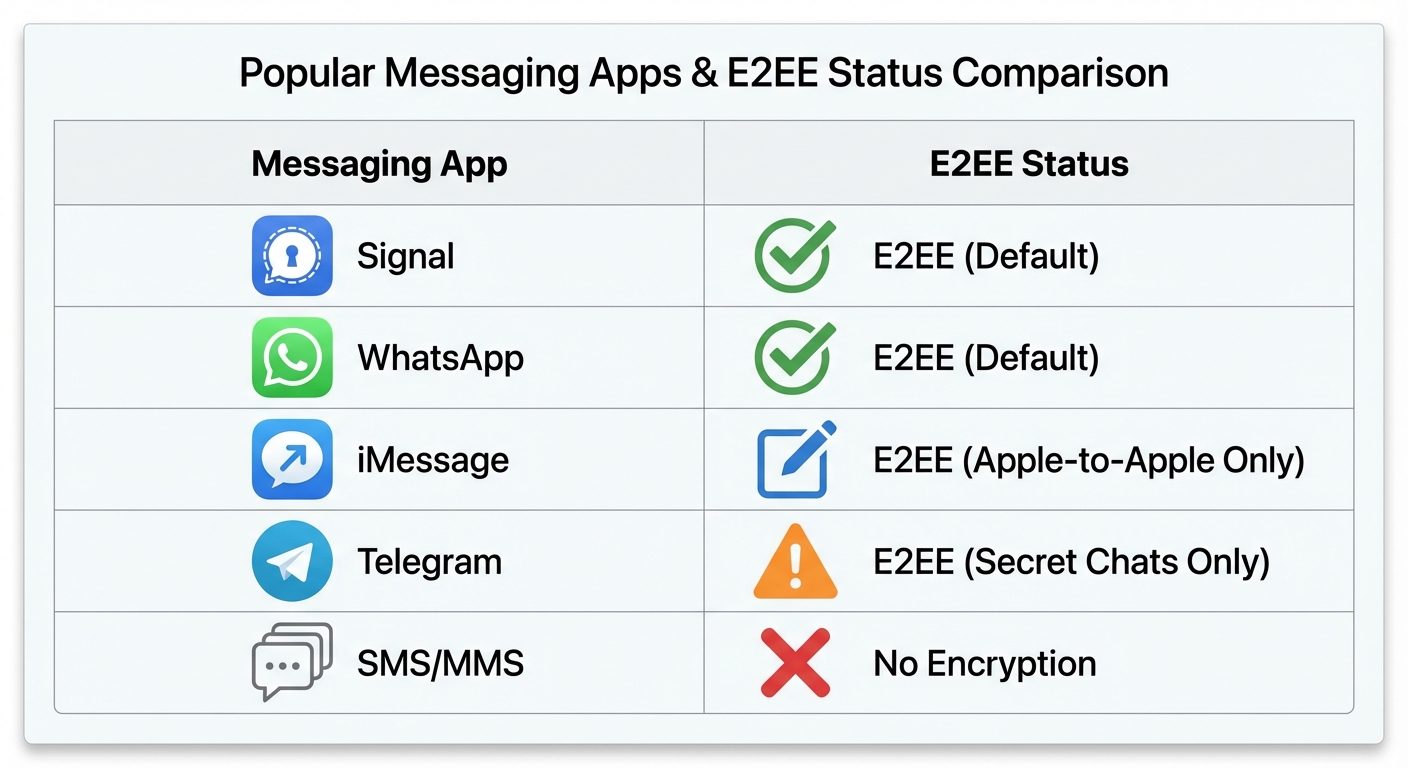
Popular Apps That Use End-to-End Encryption
Signal pioneered accessible E2EE messaging and remains the gold standard for secure communication. All messages, calls, and file transfers are end-to-end encrypted by default. Signal’s protocol is open source and independently audited.
WhatsApp implemented the Signal protocol in 2016, bringing E2EE to over a billion users. Messages and calls are end-to-end encrypted by default, though metadata (who talks to whom, when) is not.
iMessage between Apple devices uses end-to-end encryption, though messages to non-Apple devices fall back to unencrypted SMS. Apple cannot read iMessages between iPhones, but they can read SMS texts.
Facebook Messenger and Instagram now offer E2EE, with Meta rolling it out as the default after years of it being opt-in only.
Telegram is often incorrectly assumed to use E2EE by default. Standard Telegram chats are not end-to-end encrypted. Only “Secret Chats” feature E2EE, and those must be manually initiated.
What End-to-End Encryption Doesn’t Protect
Understanding E2EE limitations is important for realistic expectations about privacy.
Device security: If someone has physical access to your unlocked phone, they can read your decrypted messages. E2EE protects data in transit and at rest on servers, but not on your own device. Use a strong passcode and enable full-disk encryption.
Metadata: E2EE hides message content but not necessarily who communicated with whom, when, and how often. This metadata can reveal a lot about relationships and activities. Different services retain different amounts of metadata.
Screenshots and sharing: Recipients can screenshot, copy, or share your messages. E2EE doesn’t prevent the person you’re talking to from exposing the conversation.
Compromised devices: Malware on your phone or the recipient’s phone can read messages before encryption or after decryption. E2EE can’t protect against a device that’s already compromised.
Why End-to-End Encryption Matters
The value of E2EE extends beyond protecting individual conversations. It shifts the security model from trusting institutions to trusting mathematics.
Without E2EE, we rely on companies to protect our data, resist government overreach, and prevent employee abuse. History shows this trust is often misplaced. Companies get hacked. Governments demand access. Employees snoop. E2EE removes the need to trust, replacing it with technical assurance.
For journalists protecting sources, activists organizing under surveillance, and abuse victims communicating safely, E2EE isn’t a convenience but a necessity. It enables free speech and private communication in contexts where exposure is dangerous.
Even ordinary conversations benefit. Medical discussions, financial matters, and intimate relationships all deserve privacy. E2EE ensures that privacy without requiring you to trust a corporation with your most personal communications.
Summary
End-to-end encryption encrypts messages on your device so only the recipient’s device can decrypt them. Even the company providing the messaging service cannot read the content. This protects against company access, data breaches, and legal compulsion.
Signal, WhatsApp, and iMessage (between Apple devices) use E2EE by default. Telegram requires manually enabling Secret Chats for E2EE. E2EE doesn’t protect against device compromise, metadata collection, or recipients sharing your messages. For genuine private communication, E2EE provides mathematical assurance that’s stronger than trusting any institution.